Single Citrix Compromised Credential Results in $22M Ransom
In late February 2024 Change Healthcare suffered a devastating ransomware attack which led to major disruptions to the company’s platform, estimated at a staggering $872,000,000
The attack which was carried out by BlackCat ransomware group also resulted in a $22,000,000 ransom payment.
But how did this happen?
In a testimony by Andrew Witty, Change Healthcare’s CEO, it is revealed that the hackers gained access using a single compromised Citrix credential on an account that had no MFA in place —
“While we will learn more and our understanding may change, here’s what I can share today. On February 12, criminals used compromised credentials to remotely access a Change Healthcare Citrix portal, an application used to enable remote access to desktops. The portal did not have multi-factor authentication. Once the threat actor gained access, they moved laterally within the systems in more sophisticated ways and exfiltrated data. Ransomware was deployed nine days later.”
Hudson Rock researchers investigated the hack and identified an employee of Change Healthcare that was infected by an Infostealer on February 7th, this employee only had a single credential associated with Change Healthcare — a Citrix account:
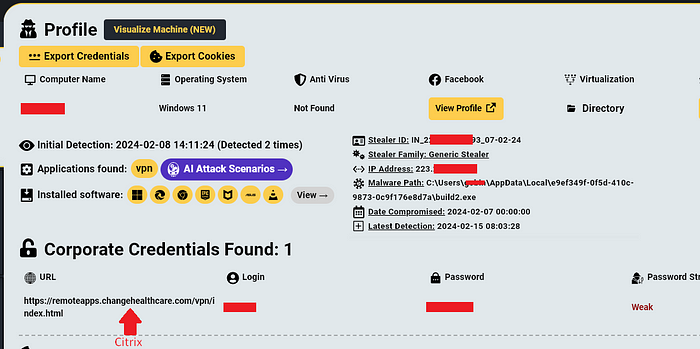
The login data which is used to access https://remoteapps(.)changehealthcare(.)com/vpn/index.html can be confirmed to be the company’s Citrix server, which no longer works, thanks to an old archive from an employee manual that was indexed on Scribd:

While it is not certain that these are the specific credentials used for the attack, in terms of timeline it matches perfectly.
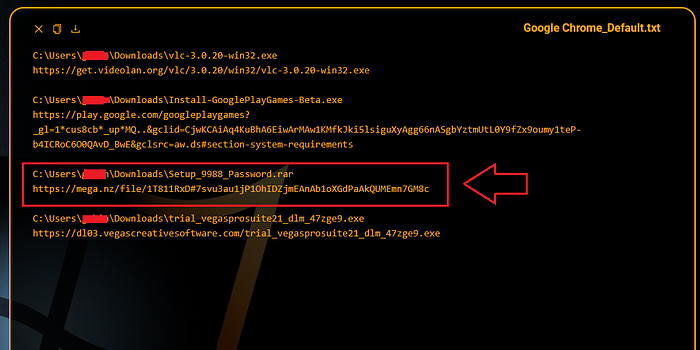
Having investigated the infected computer, Hudson Rock researchers discovered the employee was infected by downloading a file from file sharing website Mega.nz, typically threat actors attempt to get victims to download password protected RARs/ZIPs and execute them to get infected:
Credentials obtained from info-stealer infections, which have become the primary initial attack vector in recent years, provide threat actors with easy entry points into companies, facilitating data breaches and ransomware attacks.
It’s crucial to underscore that Hudson Rock had the data of this employee’s compromised data a day after the infection, highlighting a missed opportunity to preemptively safeguard against this incident.
Info-stealer infections as a cybercrime trend surged by an incredible 6000% since 2018, positioning them as the primary initial attack vector used by threat actors to infiltrate organizations and execute cyberattacks, including ransomware, data breaches, account overtakes, and corporate espionage.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
Hudson Rock provides access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools